The IB CS SL Book - Topic 3
from IB students, to IB students, for IB students
Catelogue:
- Core
- System fundamentals
- Computer organization
- Computer organization
- Computer architecture
- Secondary memory
- Operating systems and application systems
- Binary representation
- Simple logic gates
- Computer organization
- Networks
- Computational thinking, problem-solving and programming
- General principles
- Think procedurally
- Think logically
- Thinking ahead
- Thinking concurrently
- Thinking abstractly
- Connecting computational thinking and program design
- Introduction to programming
- Nature of programming language
- Use of programming language
- General principles
- Option
- Option D: Object-oriented programming
- Internal Assesment
Core
Topic 3: Networks
1. Networks
1. Network fundamentals
3.1.1 Different types of network
A Computer network is comprised of two or more computer systems that are connected and able to communicate and exchange data.
There are two key roles in computer networks:
- Server: A server can either be a computer system or a software application that provides a service to the other computer systems connected to the same network.
- Client: A client can either be a computer system or a software application that requests a service from a server connected to the same network.
There are various different types of networks can be established from the combination of servers and clients.
- LAN (Local Area Network)
LAN is a computer network that connects computer systems within a limited geographical area. (e.g. room, home, office building, school)
- Usually have high data-transfer rate between them.
- Fast network connection within LAN
- Allows the sharing of peripheral devices
- Printers, Scanners, External hard disks can be used by any computer system in the LAN.
- Does not need to buy a number of devices. One single printer can service the whole area.
- Sharing of data
- Exchange of data between clients
- Eliminate the need of exchange CDs or USB drives
- File server, etc.
- High connection speed within LAN makes transfer of data very fast. (usually 10MB/s to 1GB/s, depending on the hardware)
Mostly a LAN is constructed using a switch or hub which allows multiple network devices can exchange data and form a single network.
- VLAN (Virtual Local Area Network)
Imagine a business creates a LAN and connects all its computer systems and departments together. But in this condition, any department can access the other department's resources such as printers or data, which is not desirable.
One solution is to setup a separate LAN for each department, but it will be too costly.
A VLAN can be used to partition the initial LAN into logical separate networks. Each logical network can not access another without setup.
It is similar to building separate LANs within a initial LAN.
- Pros
- VLAN has faster performance than separate LANs
- VLAN is safer
- The formation of virtual groups are easy
- More flexible (not bounded to physical connections)
- Easier to partition resources
- Independent on the medium / physical topology
- Cons
- Management is complex
- Hardware limits: there is a maximum number of VLANs for a network
- WLAN (Wireless Local Area Network)
The difference between LAN and WLAN is that WLAN uses a wireless connection method instead of copper cable or fiber. The most common technology to provide WLAN is Wi-Fi.
- Pros
- Flexible, allow connection from mobile devices
- Does not need to connect wires (easier to install)
- Cons
- Less secured (intruders can also receive the signal)
- Slower / unstable connection (depends on signal)
- Encryption is needed for security, which makes it slower
- WAN (Wide Area Network)
WAN is a computer network that connects computer systems that are within a large geographical area. (e.g. city, country, the world)
One of the example of WAN is the Internet.
- SAN (Storage Area Network)
A SAN is a network that is created so that large storage devices can be accessible from servers in a convenient and easy way.
- Internet
The Internet is a global WAN connecting millions of computer systems.
The Internet provides an extensive number of services, including the World Wide Web (WWW). Internet itself is not WWW, but rather the WWW is a service of the Internet.
Internet is decentralized, which means its resources are not centrally stored or controlled by a single server. Contrary to most LANs and WANs, the Internet is not owned by a single entity (person or organization).
- Extranet
An extranet is a computer network that utilizes the Internet to allow controlled access by specific users to a specific LAN or WAN.
Extranet require security and privacy techniques so as the public or outside users are not permitted to access any secure data.
- VPN (Virtual Private Network)
A VPN is a computer network that connects two or more computer systems and allows clients from remote locations to connect to the network and appear to be inside the LAN as if they were physical present.
A VPN has all the benefits of a LAN: allowing users to share data and resources without compromising security. A VPN is a cost-effectively approach to connect geographically disparate offices of a business within a network with all the functionality of a single LAN.
Different from Extranet, a VPN provides a secure connection to clients, while an extranet limits access to the LAN to selected (authenticated) outsiders. VPN also provides more security since data send and received are always encrypted.
- PAN (Personal Area Network)
PAN is a network that interconnects devices that are centered around an individual person's workspace. Devices on PANs can connect both wired (typically USB) and wirelessly (Bluetooth, WiFi, etc.) An example of PAN could be Airdrop between Apple devices and connection between iPhones and Apple Watches.
- P2P (Peer-to-peer)
P2P is a network that does not utilize the client/server model. Instead, a P2P network uses a distributed network architecture where:
- all the computer systems (called node or peers) in the network are both clients and servers at the same time
- consuming and supplying resources from and to the other computer systems connected to the network.
- Need for centralized servers is removed, therefore removed bottlenecks.
One of the Example is BitTorrent download network where download source is a P2P network, therefore achieve higher download speed and allow access for resources from multiple backups.
3.1.2 The importance of standards in the construction of networks
There are different rules or protocols that need to be followed in order for the computer system involved to exchange data efficiently.
Protocol is sets of rules that ensure the transfer of data between systems.
A protocol that is recognized as the standard for a specific type of transfer is called standard protocol.
Standards play an important role in the construction of networks. Standard describe the common ground on which hardware and software manufactures can depend on in order to build systems that are able to communicate with each other.
Protocols can be understood as a common international "language" that enables compatibility for all computer systems throughout the globe.
3.1.3 Network communications and layers
In a world where all kinds of different manufatures produces different computer systems (laptops, mobile phones, desktops, servers, etc.) We need a standard (protocol) of the Internet that different maufactures can follow.
The solution is through using layers. For a program that requests data from a server, it needs to go through two basic processes:
- Pass the request through different layers
- Obtain the answer through different layers
Different layers serve different functions and use different protocols for information exchange.
Advantages of using layers:
- Easy to manage (seperated into layers)
- Greater understanding of each layer
- Common language for each layer
- Makes protocol designs easier
- A manufacturer can focus on technologies of a particular layer
- Products of different manufacturers can work together
- Technology advances of a layer are independent of technology advancements of other layers
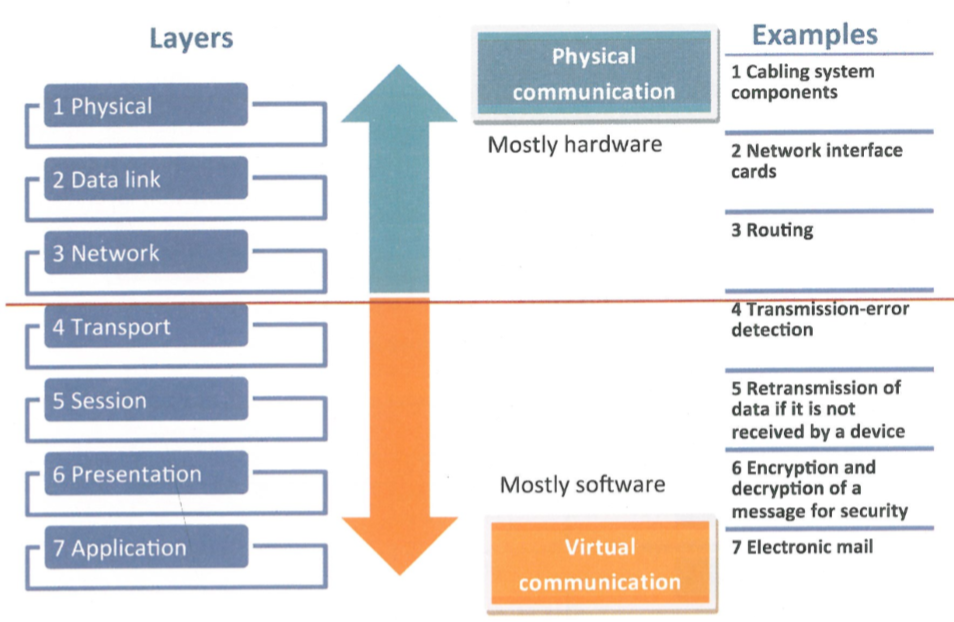
There is a reference model of layers: OSI model
OSI model: Open Systems Interconnection model. It's the reference model established by International Standards Organization (ISO) and it contains 7 layers.
These severn layers should be excatly remembered for exam.
3.1.4 Technologies required to provide a VPN
A Virtual Private Network makes a tunnelled network connection through the internet or any other public network. It's an ideal solution for establishing secured connection between private networks with remote users.
- VPN users can exchange data maintaining privacy through a "tunnelling" protocol and various security procedures.
Hardware and software requirements
- Internet access
- VPN software (client, utilities, server)
- VPN routers
- VPN appliances
- VPN concentrators (A device to handle a large number of incoming VPN tunnels)
- VPN servers
Secure VPN technologies
- Internet protocol security protocol (IPsec)
- Allows the secure transmission of data over public networks
- Use standard encryption algorithms (AES)
- Provides authentication using digital certificates
- Secure Socket Layer (SSL) / Transport Layer Security (TLS)
- Does not require specific software
- Most web servers and browsers already support this
3.1.5 Use of VPN
Benefits of a VPN
- Communication is easier
- Companies take advantage of the Internet to provide secure connections
- Decreases operational costs vs. WAN
- Employees work as they are directly in the network
- Extend connections across different geographical sites
- Improves overall productivity
- Improves productivity of remote workers
- Improves security
- Offers flexibility to employees to take advantage of the company's Internet over an existing connection
- Offers flexibility to remote offices
- Offers global networking oppurtunities
- Provides teleworker support
- Reduces environmental footprint
- Reduces travel times and cost
- Simplify network topology for administrators
2. Data transmission
3.1.6 Protocol and data packet
Protocol is sets of rules that ensure the transfer of data between systems.
A Data packet is a group of bits, which may include control signals, error control bits, coded information, as well as the destination for the data.
3.1.7 Necessity of protocols
Required protocols for communication to take place:
- Presence of identified sender
- Presence of identified receiver
- Presence of an agreed-upon method of communicating
- Presence of common language
- Presence of common grammar
- Presence of agreed-upon speed and timing of delivery
- Presence of confirmation or acknowledgment requirements